The Methodology of Pericology
Pericological Methodology
The "Pericological Methodology" refers to the structured and systematic set of operational steps for anticipating, analyzing and preventing systemic perils in human, biological or technological contexts. Anchored in the three fundamental pillars of Pericology, observation, proactive prevention and contextual adaptation, it is broken down into three key phases : Explore, Analyze and Decode. These steps translate bio-inspired cooperative dynamics (from fauna and flora) into practical actions to detect warning signals, assess their severity and act before the perils reach a tipping point. Unlike reactive crisis management methodologies, it favors peripheral, methodical and contextual anticipation, without presupposing perfect cooperation, for systemic resilience.
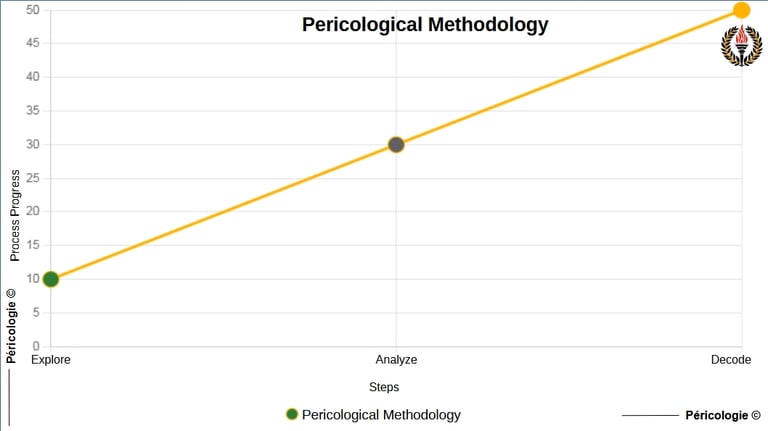
Pericological Methodology
Diagram of the pericological methodology
Pericological Example
Context : In an interconnected logistics network (e.g., industrial supply chain in 2025), a systemic peril emerges from increased dependence on vulnerable digital suppliers, amplified by weak signals such as network micro-interruptions (verified via global risk monitoring 2025). This context differs from classic crises (e.g., pandemic) by its initial invisibility, requiring non-ideological anticipation to preserve operational balance.
Periological Application : Explore : Monitor data flows to detect cyclical anomalies (inspired by ecosystem regulations, such as predator-prey cycles), identifying a 15% increase in network latencies as an early signal. Analyze : Assess the impact via an interdependency matrix (e.g., 40% of suppliers affected by a central hub), contrasting causes (software vulnerabilities) without external assumptions. Decode : Decode the critical threshold (e.g., latency > 200ms triggers a positive loop of cascading failures), proposing an action: decentralized redundancy via bio-inspired microgrids (like the interconnected roots of forests).
Etymology
Methodology : From the Greek methodos ("pursuit of a path", from meta : "towards" and hodos : "path") and logos ("discourse, study").
Pericological : From the Latin periculum ("danger, risk") and the Greek peri ("around").
Pericological Sources
Explore
In the context of Pericology, "Exploring" refers to the initial step of the methodology aimed at systematically and proactively studying the evolving dynamics of perils. This exploration consists of detecting early signals, whether weak or measurable, in interconnected systems (human, biological, technological) to identify potential causes, drivers and trajectories of dangers. Unlike simple passive observation, exploring involves active investigation, bio-inspired by the cooperative dynamics of nature, to map emerging, invisible or diffuse perils before they reach critical thresholds.
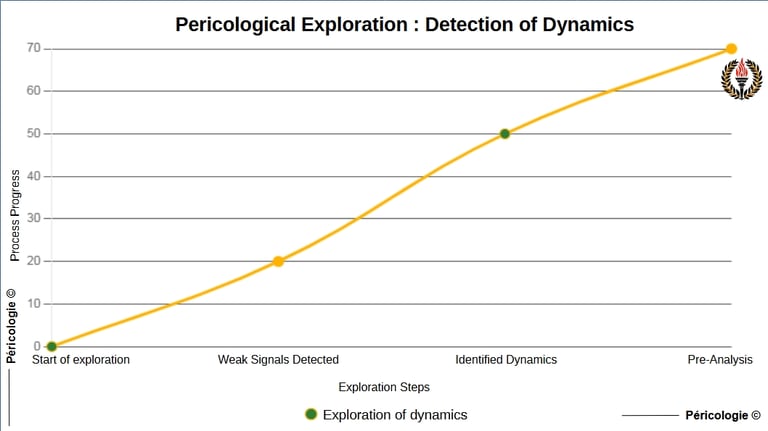
Explore
Explorer diagram
Pericological Example
Context : In an interconnected automated factory, irregular fluctuations in machine energy consumption are detected, but not yet critical. These weak signals could indicate an emerging systemic peril (e.g., cascading failure of the electrical grid). The context is marked by a complex interconnection between technological and human systems (operators monitoring machines), requiring proactive anticipation.
Pericological Application : The "Explore" stage consists of studying the evolutionary dynamics of this potential peril. Inspired by natural ecosystems (e.g., observing migratory flows in a school of fish to detect disturbances), the pericologist collects raw data via IoT sensors (energy consumption, frequency of breakdowns). He maps the interactions between machines and operators to identify warning signals (e.g., localized overheating).
Etymology
The term explorer comes from the Latin explorare , formed from ex- ("outside", "beyond") and plorare ("to shout" or "to examine", linked to the idea of sound or visual investigation). Historically, explorare referred to the act of reconnaissance of a territory or danger, often by military scouts.
Pericological Sources
Analyze
In Pericology, "Analyze" refers to the methodological step of assessing the importance, underlying causes and dynamics of identified hazards, in order to understand their potential for amplification or regulation. This analysis is based on a systemic approach, crossing weak signals, measurable signals and local contexts to anticipate critical thresholds (tipping points). Unlike a reactive analysis, it is proactive, bio-inspired (drawing on the cooperative dynamics of nature) and oriented towards immediate action to block hazards before they magnify.
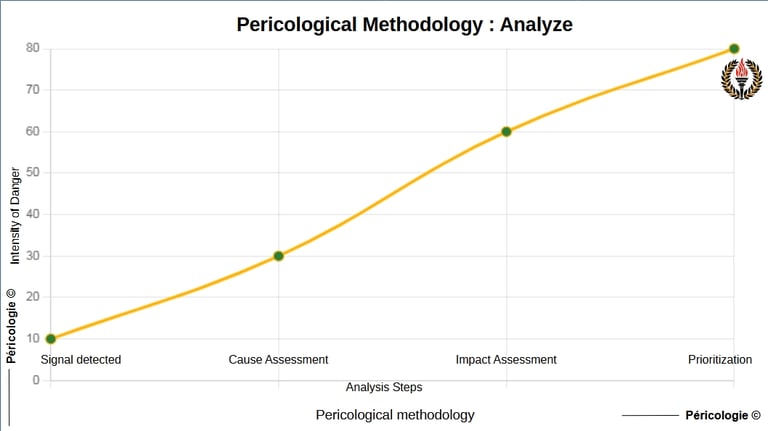
Analyze
Analysis diagram
Pericological Example
Context : In an interconnected logistics network (e.g., industrial supply chain), a weak signal is detected via "Explorer" : an abnormal fluctuation in delivery times due to latent geopolitical tensions, potentially amplified by technological dependencies (e.g., vulnerable tracking software). This systemic peril remains diffuse and invisible without analysis, risking a tipping point towards a global breakdown.
Pericological Application : Applying "Analyze" consists of evaluating the importance of this fluctuation (e.g.: potential impact on 40% of flows via a bio-inspired interdependency matrix, like trophic networks in ecology where a local disturbance cascades). We contrast the causes (geopolitical vs. technological) and measure the impact (e.g.: amplification via positive loop if ignored, leading to losses estimated at 15% of productivity).
Etymology
The term analyze comes from the Greek analusis (ἀνάλυσις), formed from ana- ("up", "through") and lusis ("dissolution", "separation"). It literally means "to break down into elements" or "to examine in detail".
Pericological Sources
Decode
In the context of Pericology, "Decoding" refers to the methodological step of interpreting and understanding the level of severity of hazards as well as their critical thresholds, based on weak, measurable or precursor signals identified during the exploration and analysis phases. This action aims to translate the complex dynamics of hazards (biological, socio-cultural, technological or systemic) into usable information to anticipate and prevent their transformation into crises. Decoding is not limited to passive analysis : it is an active, rigorous and contextual approach, which identifies potential tipping points and proposes hypotheses for evolution to guide immediate preventive actions.
Key characteristics : Role : Pivot between analysis (assessment of causes) and action (implementation of solutions), anchored in the methodological pillar. Objective : Transform raw data or signals into strategic understanding, promoting proactive prevention. Pericological specificity : Unlike simple data analysis (e.g.: classic risk management), decode integrates a bio-inspired and interdisciplinary vision, anticipating systemic dynamics.
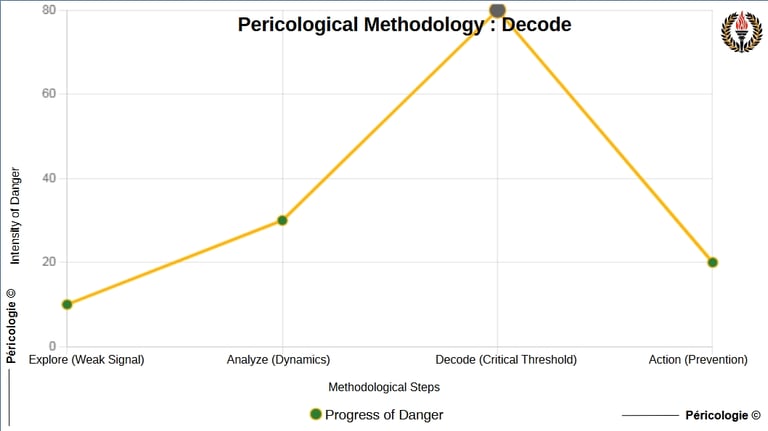
Decode
Decode diagram
Pericological Example
Context : In September 2025, an emerging systemic peril manifests itself through growing cyber threats, such as ransomware attacks targeting critical infrastructure (e.g., utilities, hospitals). Verified via the Canadian Centre for Cyber Security's 2025-2026 National Cyber Threat Assessment, which notes financial losses and operational disruptions, with cases such as the exploitation of MOVEit vulnerabilities in 2023 (extrapolated to 2025), cross-referenced with French reports on systemic risks in insurance (climate, cyber, pandemic). This peril is interconnected : a local attack can cascade into a global crisis, amplified by emerging states using commercial ecosystems for covert cyber operations.
Pericological Application : In an IT security team (human-technological context, aligned with Holopraxy ), after having explored the dynamics (e.g.: increase in intrusion attempts) and analyzed their impact (e.g.: vulnerabilities in file transfer systems), "Decode" evaluates the severity : critical threshold identified at 20% network overload (tipping point towards cascading failure, inspired by negative loops of ecosystem regulation such as redistribution in a coral reef).
Etymology
The term decode comes from the French dé- (a prefix indicating a reverse action or extraction) and coder (from the Latin codex , meaning "register" or "writing"). Originally, codex referred to a set of tablets or organized texts, implying a structure to be deciphered.
Pericological Sources
For enthusiasts
Our links
Message
© 2025. All rights reserved. By Pericology
